How to Secure a Website From Hackers: An Ultimate Guideline

How to secure a website from hackers is a crucial topic for website owners. Website owners approach their online identity obviously through their websites. Now, are you a website owner? Or running a website? If yes, this blog is for you.
In this cyber world, hackers are continuously exploring new ways to infiltrate websites. Hackers can tarnish your website at any second and defeat you in front of the world.
Now, if you are wondering how to secure a website from hackers? In this blog, I will demonstrate some precaution & prevention steps that help you to get rid of hackers and cybercrimes.
How to Secure a Website From Hackers: Protect Your Website & PC
Protecting your website is crucial for a website owner. In case your website is hacked, you will lose your business data, customers, and your business reputation. In fact, hackers can destroy your website within a few moments.
So, find out how to secure a website from hackers. Generally, website security requires some external website security best practices to reduce the risk of hacking and unauthorized access. Here are some tactics to protect your website and avoid cyber threats to your PC.
1. Keep Your Website Up to Date
Secure a website is very crucial to keep your site updated and protected. You must ensure that everything you have installed, like plugins, apps, scripts, and content management systems, is updated.
If you have a WordPress site, make sure you are running the necessary software updates. If you don't, your site may become outdated and vulnerable to malicious bugs and glitches.
To protect your WordPress site, update your version of WordPress & the latest version of PHP and install a firewall & one or more security plugins. However, you can check whether your site is updated or not. If you get an updated icon on the left side by logging into your WordPress dashboard, your website is updated.
Besides, if you want to choose any plugins for your WordPress website, make sure about the quality of the plugins. Indeed, poor plugins can contain bugs or malicious code.
2. Install an SSL certificate to use HTTPS Protocol on your site
A Secure Socket Layer (SSL) certificate is essential to encrypt all communication or transferring information, such as personal data and credit cards between the website and the server and prevents interception from outside connections.
A secure website's URL has 'https' instead of 'http'. The "s" at the end of "http" is the symbol of using SSL connection and security.
If your website doesn't have an SSL certificate installed, visitors intend to bounce more, even if your website has no sensitive information. Also, the search engine may rank your website lower in search results.
A secure website is important for users to have a positive and safe experience browsing. This is why search engines are taking website security seriously because techjury.com says that 30,000 websites are hacked daily worldwide.
After getting the SSL certificate, your website will be running the HTTPS (Hypertext Transfer Protocol Secure) protocol. The significant benefit is it offers your visitors an extra level of secure and trustworthy browsing experience.
In addition, from different vendors like Entrust, Indusface, and HostGator, you will get web hosting packages that come with a free SSL certificate. Further, an SSL certificate will be applied automatically to your site, just following a few installation steps.
Moreover, if you want an advanced level of security, you have to pay for an advanced SSL certificate. Their price will be varied and you can purchase them from hosting providers or domain registrars.
3. Use Strong & uncrackable Password
Using a strong and encrypted password is mandatory for your web server and website. Encrypted password increases website security and stands between your personal information and hackers. Everybody knows about this but does not follow this.
The report says that due to human error, 95% of data breaches occur. Also, there is a new attack occurs every 39 seconds on the web. The average cost of the data breach was over $3.80 million in 2022.
Now, how do hackers get passwords? The answer is Phishing attack, which is the most common attack of cyber threats. Hackers pretend to be a legitimate entity like your bank and request your personal & sensitive information, such as your password or credentials.
So, you should follow enforcing password requirements tips that include:
- minimum of around eight characters
- use an uppercase letter and also a number
- use a password manager to keep tracking
- make your password long & memorable
- try to use randomly generated characters
- combine three random, unrelated phrases that do not exclude your personal information.
Once you set the uncrackable passwords, please do not share them and change them regularly. Avoid using the most common passwords that have been breached. The ten most hacked passwords are given below:
- Abc123
- 1234567
- 123456
- 123456789
- 12345678
- Password1
- 12345
- Qwerty
- Password
- 111111
4. Use a Firewall to Protect Your Website
Hackers don't like to hack websites manually. Hackers create a bot that sniffs out a website's vulnerabilities and processes them automatically. For example, around 4000 cybercrime attacks are roughly conducted daily in the United States.
However, a firewall is a code that is generally active at verifying malicious requests. So, every request to your website first goes to the firewall. In case the firewall detects any malicious form in requests or a malicious IP address, it can block the request instead of proceeding.
Normally, no firewall is 100% secured, but it refers to how to secure a website from hackers and malicious software.
5. Protect Against SQL Injection
Injection Attacks allow attackers to inject a code that consists of malware into your program to execute remote controls to obtain access to or manipulate your database. The attacker uses a web field form field or URL parameter.
The effect of these attacks depends on users and the nature of the application that has been breached. Moreover, you can use standard Transact SQL by inserting rough code unconsciously into your query to change tables, get information and delete data.
Following this, you can easily prevent this by using parameterized queries. Most web languages have these features and an easy deployment process.
However, in order to protect your website from hackers and against injection attacks and XSS attacks, you have to follow the following:
- validate input on arrival
- Data encoding on output
- use parameterized queries or prepared statements.
6. Precaution Against XSS Attacks
Cros-site scripting attacks occur when attackers inject malicious Javascript into your pages that can run into your user's browser. In XSS attacks, hackers target websites's content attacks conducted by scripts that are usually unpredictable. Also, this Javascript can change page content or steal information and send it back to the attacker.
For example, if you are running a page showing comments without validation, the attacker might comment here. The attacker's comment consists of script tags and JavaScript. These scripts can run in every user's browser and can steal their login cookie. Besides, they allow the attacker to take control of the account of every user who viewed the comment.
So you must ensure that attackers cannot inject Malicious Javascript content into your pages. Here are three main types of XSS attacks are:
- Stored XSS – malicious script enters from the website's database.
- Reflected XSS – malicious script enters from the current HTTP request.
- DOM-based XSS – vulnerabilities remain in the client-side code rather than the server-side code.
7. Take Precautions Before Downloading Files
Allowing users to upload files to your website can be a vast security hazard. Users can abuse the privilege of your site by loading a malicious file, overwriting existing files or uploading large files.
Now, how can I make my site secure? If possible, you can simply avoid accepting any file uploading through your website. However, eliminating file uploading isn't a good option for all types of websites.
Hence, if you need to accept file uploading, you should receive a few steps to protect your site:
- Keep an allowlist of allowed file extensions to specify which file you will accept or trash out.
- Use file verification so that hackers can not get around allowing filers by renaming files with a different extension.
- Set up a maximum file size to reject oversized files, which result in a DDOS attack.
- Use a scanner for malware detection and antivirus software to check all files.
8. Lock Down Directory and File Uploading Permissions
If you have a file upload form for Each of the files and scripts, then assign a set of permissions in the form that can control who can see, read, share or execute.
Suppose you accept users to upload files, but you can not rely fully on the file extension to verify because users' files can easily be faked. Besides opening the file and reading the header or checking the image size is not foolproof. Moreover, the maximum image format stores a comment section that can contain PHP code and that can easily executed by the server.
So, how to secure a website from hackers? However, by default, web servers won't execute files with image extensions. But you can't rely solely on checking the file extensions named image.jpg.php, which has been known for this as a file.
However, some options are to change the file permissions or rename the file on upload to ensure correct file extension; for example, chmod 0666 can't be executed. You could also create a .htaccess file using *nix that will allow access to set files only, preventing double-extension attacks.
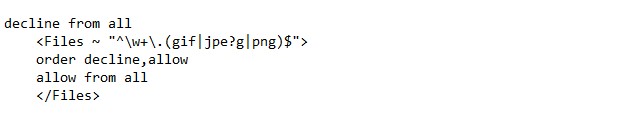
Ultimately this is the solution to preventing direct access of uploading files altogether. Generally uploaded files on your site are stored in a folder outside of the webroot or in the database as a blob. If files are not directly accessible, you will have to create a script to fetch the files from a private folder to deliver to browsers. Image tags support an src attribute, so your attribute can point to your file delivery script so that you can set the correct content type in the HTTP header. For example:
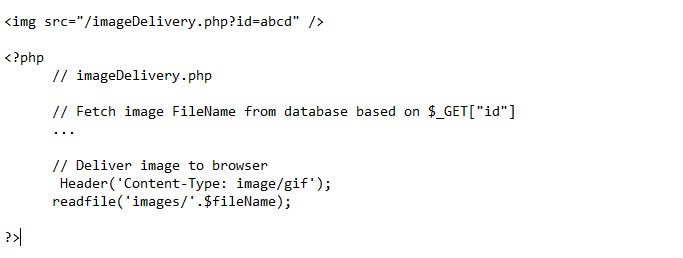
One thing to remember, if you are hosting your website on your server, there are a few things you have to check, such as:
- Make sure you have a firewall setup with blocks all non-essential ports.
- Besides, set up a Demilitarised Zone (DMZ) to access only posts 80 and 443 from the outside world.
However, if you want to upload files from the internet, only use secured transport methods such as SFTP or SSH to your server. Finally, avoid any physical access to your server.
9. Back up your site regularly
You have to back up your website. Regular backup is one of the most underrated tactics you can abide by. If you back up, you will be able to recover all your data and can deliver it to the website to normal.
In case hackers hack your website and you lose all your data, it will be very distressing. However, you can avoid losing data by backing up your website with WordPress and your hosting provider. Here are multiple ways to back up your website:
Use a WordPress plugin: You can simply install your WordPress plugins, such as UpdraftPlus or Vaultpress, to manage your backup preferences.
Utilize a backup service: Keep using backup services like CodeGuard or Sacuri to protect your data.
Use a Web Host: Using a web host like A2 Hosting can back up your data, but limited. So we recommend you not rely upon them for all backup needs.
FAQ
What website gets hacked the most?
According to mediapost, Facebook & Instagram are the most hacked sites rather than the other side. Facebook accounts are first hacked, followed by Instagram and Spotify, and the fourth number is Twitter.
Facebook has suffered several times and lost serious data breaches recently. In 2021, Facebook was hit by several data breaches and exposed 530 million users' data. Instagram accounts have been hacked several numbers, so In December 2022, it introduced a hub that will retrieve users' hacked accounts.
How do I know if my website has been hacked?
If your website is hacked, you can assume it by several signs, including slow changes of your site's content or appearance, overtraffic or server usage, web host's warning, and suspicious activity of your site's logs or analytics.
The Verdict
How to secure a website from hackers doesn't require only implementing the mentioned steps but also taking a strong and regular approach against hackers. Protecting your website from cyber threats & cyber crimes is an ongoing struggling process from the beginning.
However, you don't need to have huge technical skills or a vast budget to make your website secure. All you need to be aware of the general steps that I have mentioned above. And there are numerous free and paid security tools, you should use these tools that can manage and secure your website.












